Digital transformation is a necessity for survival today. It unlocks significant value for an organization across the entire value chain. However, the transformation journey is not without risks, the most critical of which is data breaches and cyber security threats. In this article, we cover these risks and the proactive measures your organization can take to safeguard your data during digitalization
In 2018, hotel chain Marriott Starwood International revealed that the names, addresses, phone numbers, payment information, email addresses, and passport numbers of up to 500 million customers had been hacked. Marriott was fined 124 million dollars (later reduced to ~ 23.7 million dollars) by the UK regulatory body, the Information Commissioner Office (ICO), for ‘… not having done more to secure its systems’. A separate fine of ~ 265000 dollars was imposed by the Turkish data protection authority.
Amid the potential threat, it might seem that digital transformation is not worth the investment for an organization. The reality however is that the overwhelming benefits of digitalization far outweigh the risk.
Digitalization increases the efficiency and agility of an organization’s process, boosts employee morale, and provides insight that opens up the company to more revenue streams.
So, the question isn’t whether you’ll start (or continue) your organization’s digital transformation journey, it’s how you can remain secure during the course of the journey.
Cloud vs. Local servers
One of the key questions organizations are faced with is whether to store data onsite on local servers or offsite on a cloud platform. In the former, businesses host their networks, and store data within the organization, and in the latter, data storage is enabled on the cloud often through third-party providers from where it can be accessed by stakeholders – and the general public.
While the idea of hosting data on a cloud platform where anyone can gain access may be daunting, the cloud still offers a lot more than local servers in terms of efficiency and security – including network resilience in case of fire outbreaks and natural disasters.
Furthermore, cloud servers in remote locations are physically out-of-bounds to malicious actors who will have to come up with ‘creative’ ways to gain intrusion as opposed to local servers where anyone with a drive and guile can steal sensitive information.
How to safeguard against security threats before, during, and after digital implementation
A data breach puts a lot at stake – years of financial and reputational damage can occur in one swoop, or like the Marriott breach, across a period of time. Fortunately, you can take proactive measures to forestall threats before they infiltrate your network. These measures are outlined below:
- Talk to the experts
- Integrate your systems
- Educate your employees
- Make security a parallel journey
- Protect your data
- Use technology
- Test your systems
Talk to the experts
Starting your digital transformation on the right course can be the difference between a successful program and a botched operation. Whether you are hosting on your local servers or on a cloud platform, the foundation of your digital journey should be strong with a lightweight and secure code that renders the system impenetrable to malicious actors. With so much at stake and so much to get right, the journey to digital transformation can be long and arduous. But thanks to security experts, it doesn’t have to be lonely.
Integrate your systems
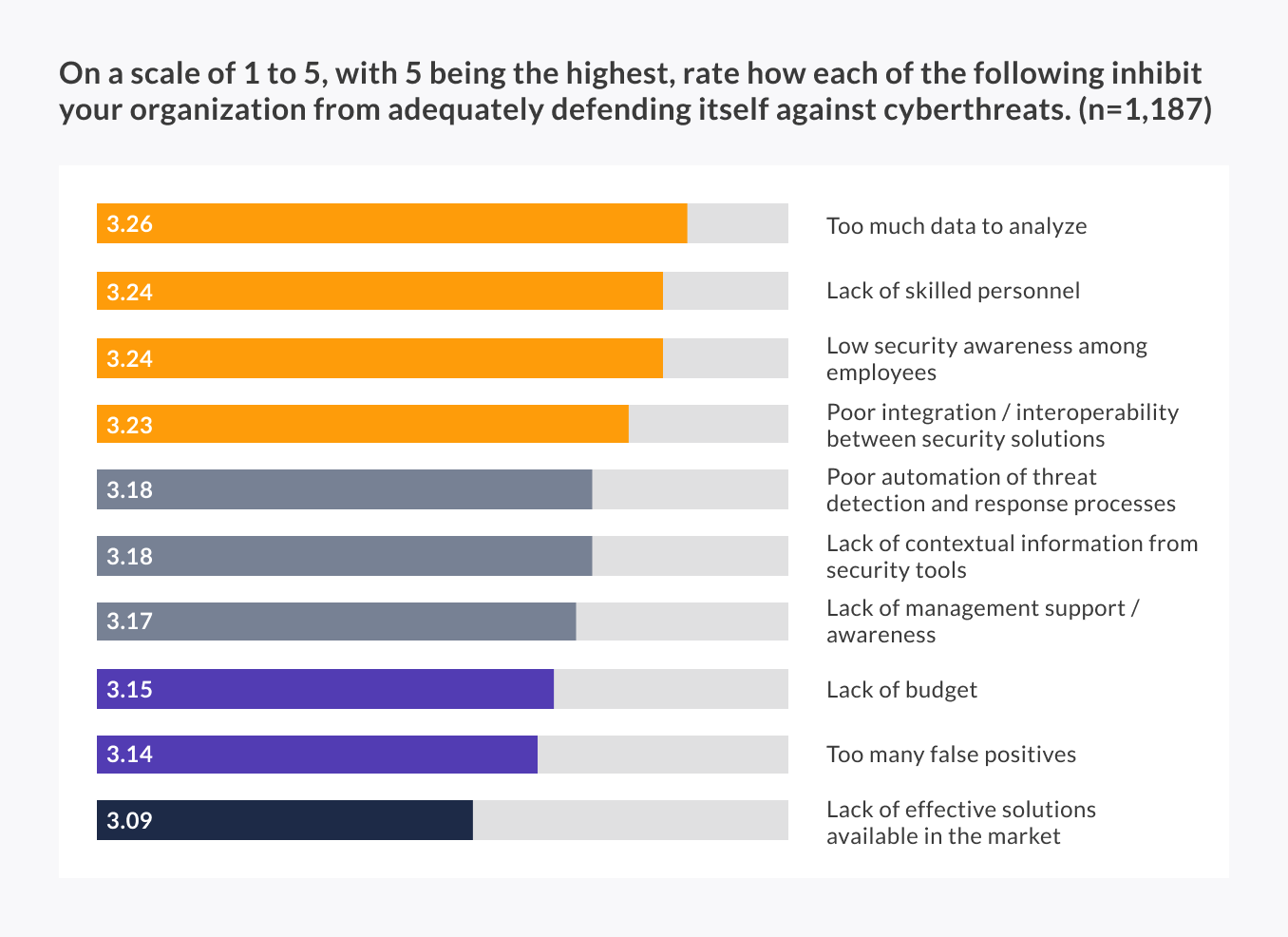
‘Data tsunami’ is the number one obstacle to achieve effective cyber threat defense. – IT security leaders, 2019.
Similar to a military frontline, your organization’s digital security is only as strong as its weakest point. The more your digital solution vendors – and the associated apps, devices, and data, the more vulnerabilities exist in your system. Hackers can target an ‘abandoned’ vendor and use that as a pathway to steal more data.
When you integrate your solutions and connect to a central ‘hub’, your teams will have greater visibility to monitor uncharacteristic behavior across the system. They can prevent attacks, manage the network, and easily police large swathes of data – a task far more difficult with siloed, multi-vendor data points. A platform-approach to digital transformation helps with just this.
Educate your employees
Sometimes, a ‘simple’ human error can be all a cybercriminal needs to gain access into a sophisticated and seemingly impenetrable system. An employee who understands the risk of a data breach and can forestall cyber threats is your first defense in the digital transformation journey.
With this in mind, you should organize regular, inclusive training for your employees where they can learn about the latest threats and understand their role in the security of the entire organization. Here again, a digital knowledge base ensures employees are aware of safety protocols and can access them at any time. Clear communication channels should be established for employees to report and share threats with stakeholders.
Make security a parallel journey
85% of chief information security officers view security issues related to digital transformation as having a somewhat to extremely large effect on their companies – Fortinet survey
Security goes alongside digitalization and upping the security ante as more data is put online is key to ensure your systems are always up to date and ready to withstand a cyber-intrusion.
Cybercriminals are always on the lookout for more ‘innovative’ ways to attack organizations and to remain satisfied with outdated security protocols means opening your organization up to cyber-intrusion. The training programs, security consulting, and data protection are a part and parcel of the transformation journey and should continue, even after full digitalization.
Protect your data
Internal data protection is your organization’s opening gambit to withstand a cyber-attack. Simple techniques like encryption, two-factor authentication, advanced permission management, and data loss prevention safeguards, can thwart cyber criminals at the first point of entry, making it difficult to gain access through employee log-in details.
Advanced permission management is particularly relevant to guard ultra-sensitive information and ensure that only authorized employees have access to such data.
Embrace technology
It takes an AI to defend against AI
Cybercrime is increasingly sophisticated and these days can be AI-enabled. An offshoot of this is the chameleon-esque polymorphic attack that can disguise itself to avoid detection while wreaking havoc on an organization’s system.
Advanced technology like artificial intelligence and machine learning can be deployed to shore up your security defenses, monitor threats in real-time, and make up for skill gaps within your team.
Test your system
An organization can offer friendly hackers financial incentives to find security flaws within its system in a controlled environment. These hackers will have superior technical skills and can determine critical vulnerabilities in a way that IT personnel cannot.
White hat hackers can be found on the HackerOne platform, a self-described ‘vulnerability coordination and bug bounty platform that connects businesses with penetration testers and cyber-security researchers.
Maximl has implemented on-cloud deployments for industrial leaders. Our security experts can guide you through every phase of your digital transformation journey to enable total integration, scalability, and visibility.



